It could be difficult to detect insider threats for the reason that common security solutions like firewalls and intrusion detection programs give attention to external threats.
Find out how businesses should make use of the KEV catalog within their vulnerability administration prioritization framework.
Obviously, it’s more challenging than ever before for security leaders to rent, coach, and retain security talent to team their packages and operate their SOCs.
Kroll’s ransomware preparedness evaluation can help your Group keep away from ransomware attacks by examining fourteen very important security places and attack vectors.
Instruction should be appealing, pertinent, and actionable. Different teams may well need certain teaching; a business could possibly give a standard training course on phishing attacks and a certain study course for builders on safe coding.
AI improves different aspects of cybersecurity, specifically the detection of, and response to, destructive pursuits. AI algorithms can identify unknown vulnerabilities by examining designs derived from earlier attacks.
The widespread usage of e-mail and internet shopping also requires adequate precautions to your id and credit score defense.
Subscribe now Know much more Get in touch with our team top computer security companies Join with our numerous group of IBM professionals that will help you make your up coming significant shift.
By combining id fraud and scam data, Javelin founded that the full losses from the US were being as high as $52 billion, with 42 million victims. Hence, failing to shield your id could see you struggling an identical fate.
Provided the increasing chance and influence of third-celebration compromise, these evaluations are significant. If suppliers or distributors with use of crucial company data are compromised due to very poor cybersecurity tactics, organizations are in danger, no matter their particular CSF 2.0 compliance.
At any given time when margins in several industries are razor skinny, bearing the price of a breach could make sizeable economical hardship or maybe jeopardize the Firm’s upcoming.
Specialist Idea MXDR builds on the existing capabilities of MDR and extended detection and response (XDR). It brings together each human expertise and the most up-to-date digital instruments to enable sturdy information assortment and correlation capabilities In combination with steady threat hunting, risk monitoring, and incident response — all shipped for a services. In the mean time, MXDR is considered the highest protection regular offered out there.
Its security product or service exams have already been persistently great, like in the most recent MITRE endpoint security assessments and CyberRatings firewall checks. Analysts predict the 19-calendar year-aged business will improve its annual profits at an eighteen% rate above the next five years.
Penetration testing (or “pen testing”) is a crucial cybersecurity services that evaluates the security posture of techniques by simulating cyberattacks. It provides an extensive technique for determining vulnerabilities, surpassing the scope of common vulnerability assessments.
 Anthony Michael Hall Then & Now!
Anthony Michael Hall Then & Now!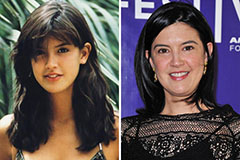 Phoebe Cates Then & Now!
Phoebe Cates Then & Now!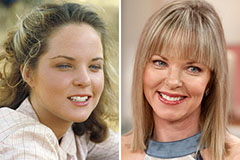 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now! Tina Louise Then & Now!
Tina Louise Then & Now!